Labour Highlights : How to manage information security risk
Cyber Risk Management Must Be Part Of Enterprise Risk Management
Every organization should have a comprehensive enterprise risk management in place that addresses four categories:
- Strategy: High-level goals aligning and supporting the organization’s mission;
- Operations: Effective and efficient use of resources;
- Financial reporting: Reliability of operational and financial reporting;
- Compliance: Compliance with applicable laws and regulations.
Cyber risk transverses all four categories and must be managed in the framework of information security risk management, regardless of your organization’s risk appetite and risk sensitivity.
HOW TO THINK ABOUT CYBER RISK
Cyber risk is tied to uncertainty like any form of risk.
As such, we should use decision theory to make rational choices about which risks to minimize and which risks to accept under uncertainty.
In general, risk is the product of likelihood times impact giving us a general risk equation of: risk = likelihood x impact.
IT risk specifically can be defined as the product of threat, vulnerability and asset value: risk = threat x vulnerability x asset value.
What is a threat? A threat is the possible danger an exploited vulnerability can cause, such as breaches or other reputational harm. Threats can either be intentional (i.e. hacking) or accidental (e.g. a poorly configured S3 bucket, or possibility of a natural disaster).Think of the threat as the likelihood that a cyber-attack will occur.
What is a vulnerability? A vulnerability is a threat that can be exploited by an attacker to perform unauthorized actions. To exploit a vulnerability, an attacker must have a tool or technique that can connect to a system’s weakness. This is known as the attack surface.It’s not enough to understand what the vulnerabilities are, and continuously monitor your business for data exposures, leaked credentials and other cyber threats. The more vulnerabilities your organization has, the higher the risk.
What is asset value? Arguably, the most important element of managing cyber risk is understanding the value of the information you are protecting. The asset value is the value of the information and it can vary tremendously. Information like your customer’s personally identifying information (PII) likely has the highest asset value and most extreme consequences.PII is valuable for attackers and there are legal requirements for protecting this data. Not to mention the reputational damage that comes from leaking personal information.
HOW TO MANAGE INFORMATION SECURITY RISK
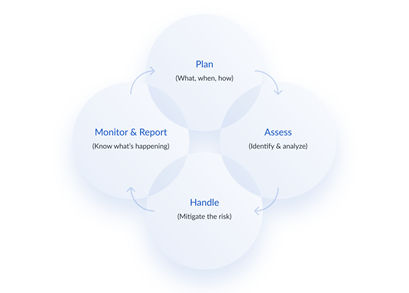
Good news, knowing what information risk management is (as we outlined above) is the first step to improving your organization’s cybersecurity.
The next step is to establish a clear risk management program, typically set by an organization’s leadership. That said, it is important for all levels of an organization to manage information security, as vulnerabilities can come from any employee and it is fundamental to your organization’s IT security to continually educate employees to avoid poor security practices that lead to data breaches.
This usually means installing intrusion detection, antivirus software, two-factor authentication processes, firewalls, continuous security monitoring of data exposures and leaked credentials, as well as third-party vendor security questionnaires.
CONCLUSION
Cybersecurity risk management is an important part of the lifecycle of any project. Organizations need to think through IT risk, perform risk analysis, and have strong security controls to ensure business objectives are being met.
However Risk avoidance isn’t enough. Organizations with information security policies but no security programs to protect their IT systems have insufficient security management practices.











